
FRAUD PREVENTION
Your financial security matters. We never request PIN, passcodes, User IDs, or passwords by phone, text, or email. Call 888.769.3796 if you suspect identity theft or fraud.

Johnson Financial Group will never contact you via email, text or phone and ask you to provide your account number, user ID or password, social security number, PIN, one-time passcode or answers to your security questions.
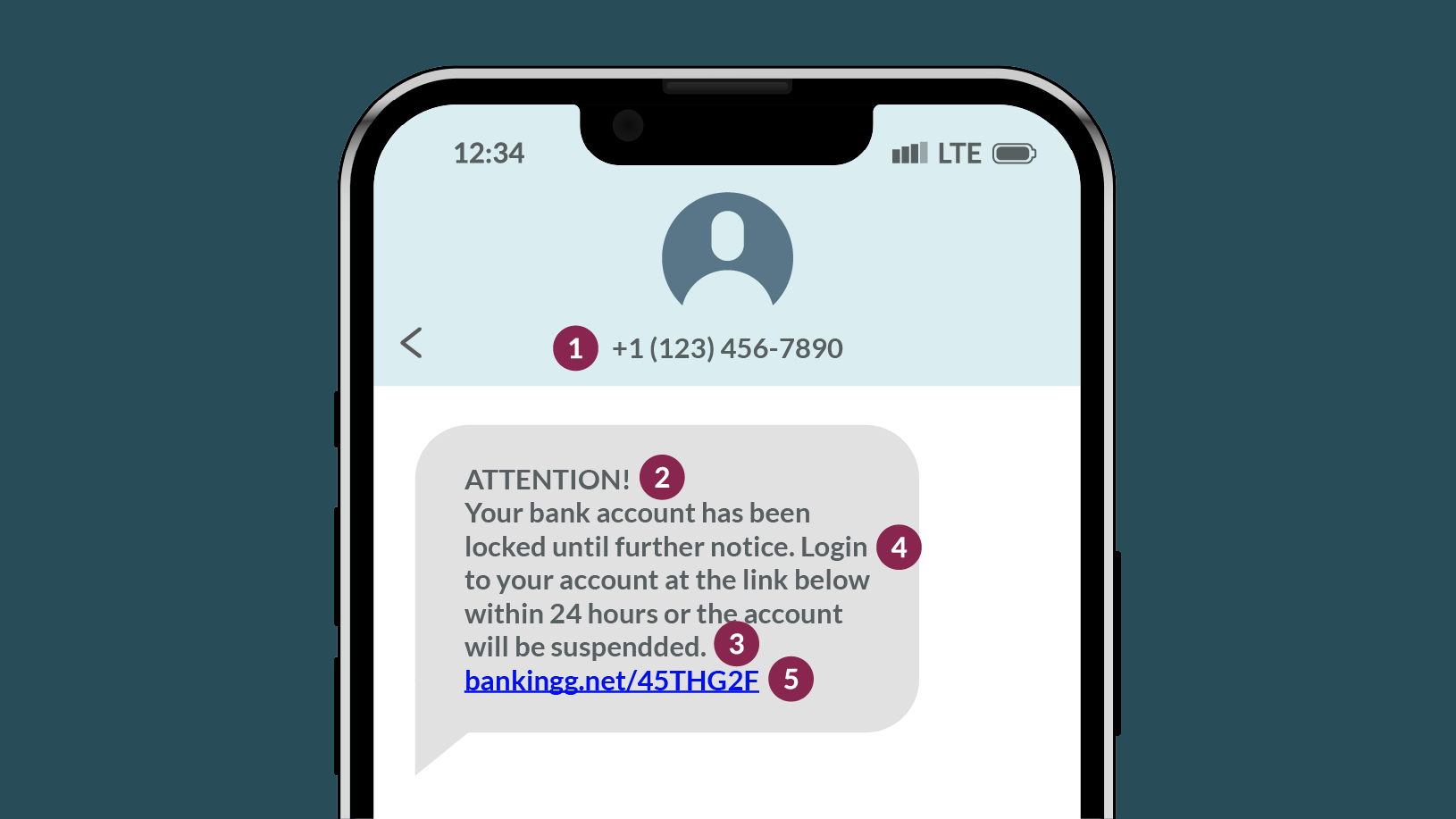
Is that the number your bank usually uses to send text messages? Legit text message updates come from “short codes,” official 5- or 6-digit numbers used by your bank.
Phishing texts try to create a sense of panic, such as threatening to suspend your account or urging you to log in to verify.
If you see misspelled words or odd grammar, they are all clear signs of an impersonator.
If a text message requests personal or sensitive information, such as account numbers, PINs, passwords or social security numbers, you can assume it’s a scam.
Banks rarely — if ever — send links via text. Don’t click them. Instead, verify the message by visiting your bank’s official website, or calling the number on the back of your card.
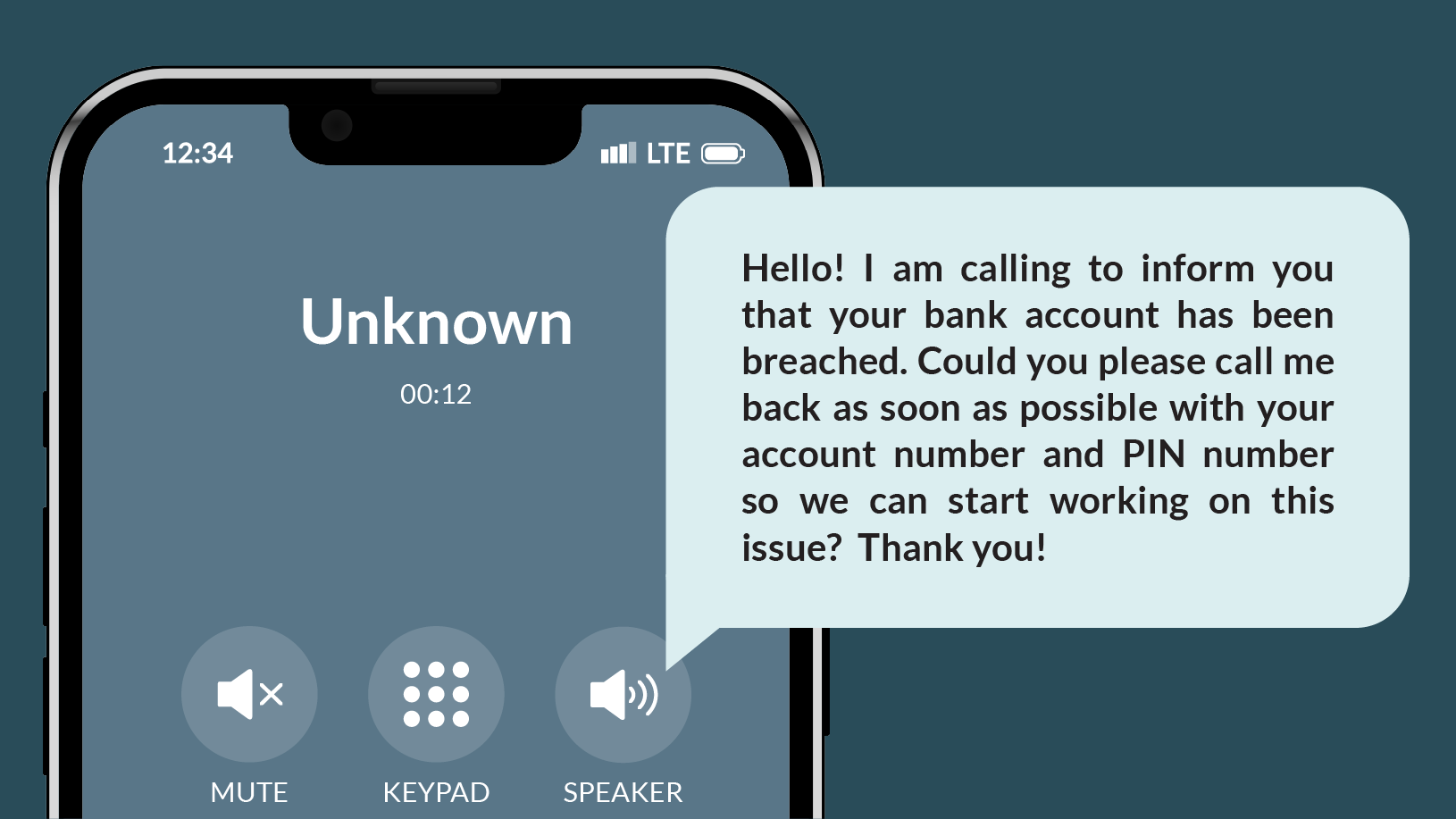
While caller ID can be spoofed, legitimate calls from your bank are more likely to display an official phone number or a known identifier. If not, be very skeptical.
Phishing calls rely on a sense of urgency. If the caller pressures you into immediate action or threatens negative consequences, just hang up and call the number on the back of your bank card.
Banks will rarely ask for your account number, PIN or password during a phone call — and will never ask for a one-time login code. Never share such confidential details unless you’ve called the number on the back of your bank card.
Be very skeptical of calls you receive out of the blue. Normally, bank representatives will only reach out if you initiate contact first. Stay safe by ending the call and dialing the number on the back of your bank card.
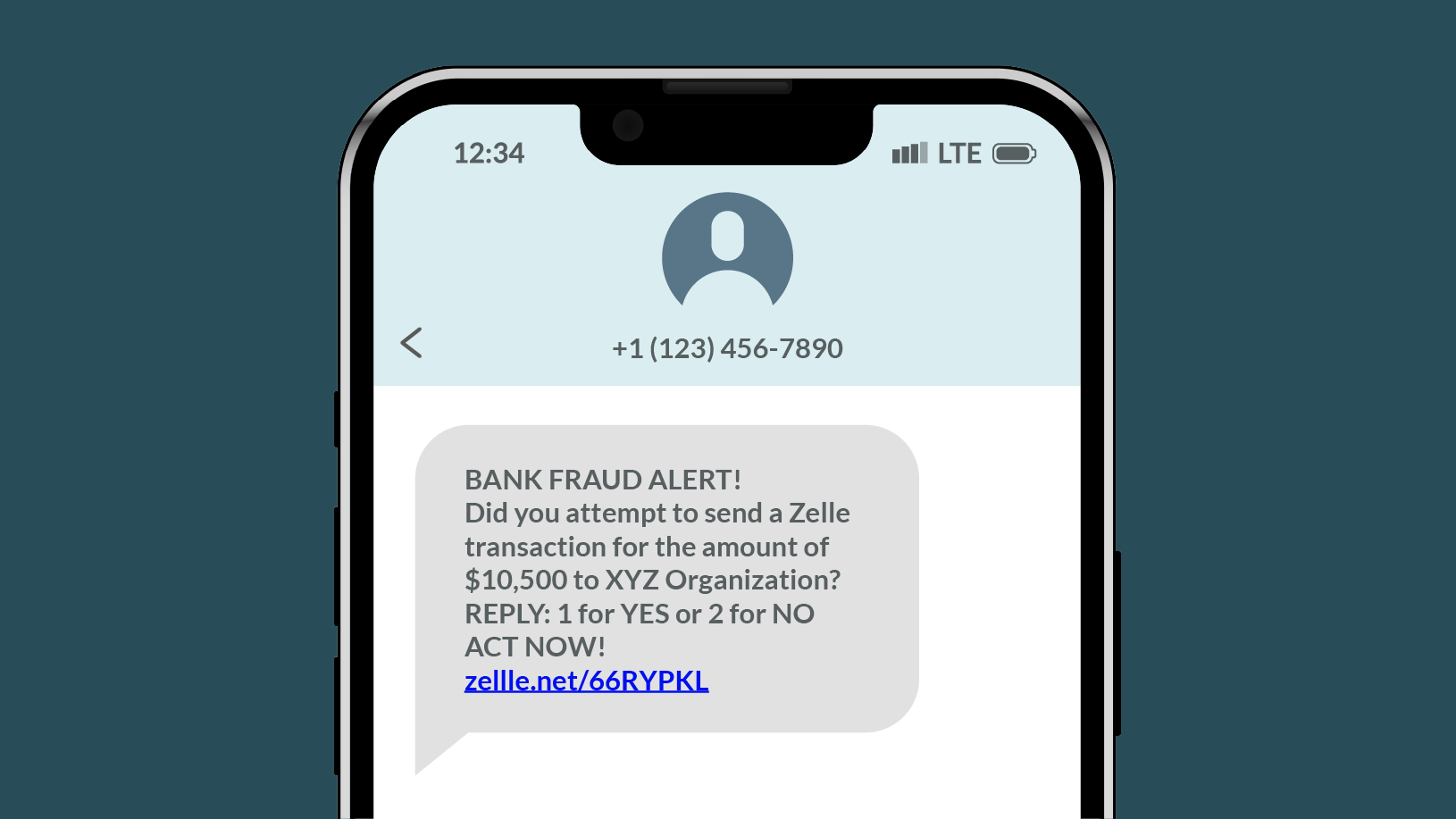
Be cautious if you receive unexpected requests from strangers or organizations asking you to send money through a payment app.
If someone who claims to be your bank says you have to send money to yourself, you can be certain it’s a scam.
Be skeptical if a sender claims to have accidentally overpaid you through Zelle® and requests a refund of the excess amount. Scammers use this tactic to trick you into sending them money.
If you receive a payment app-related message that contains a link, never click it. Scammers often send links to fake login pages to steal your username and password.
Scammers attempt to trick you by creating a sense of urgency. If they mention unforeseen emergencies, unverified transactions, account suspension or unsolicited prize winnings, it’s a scam.
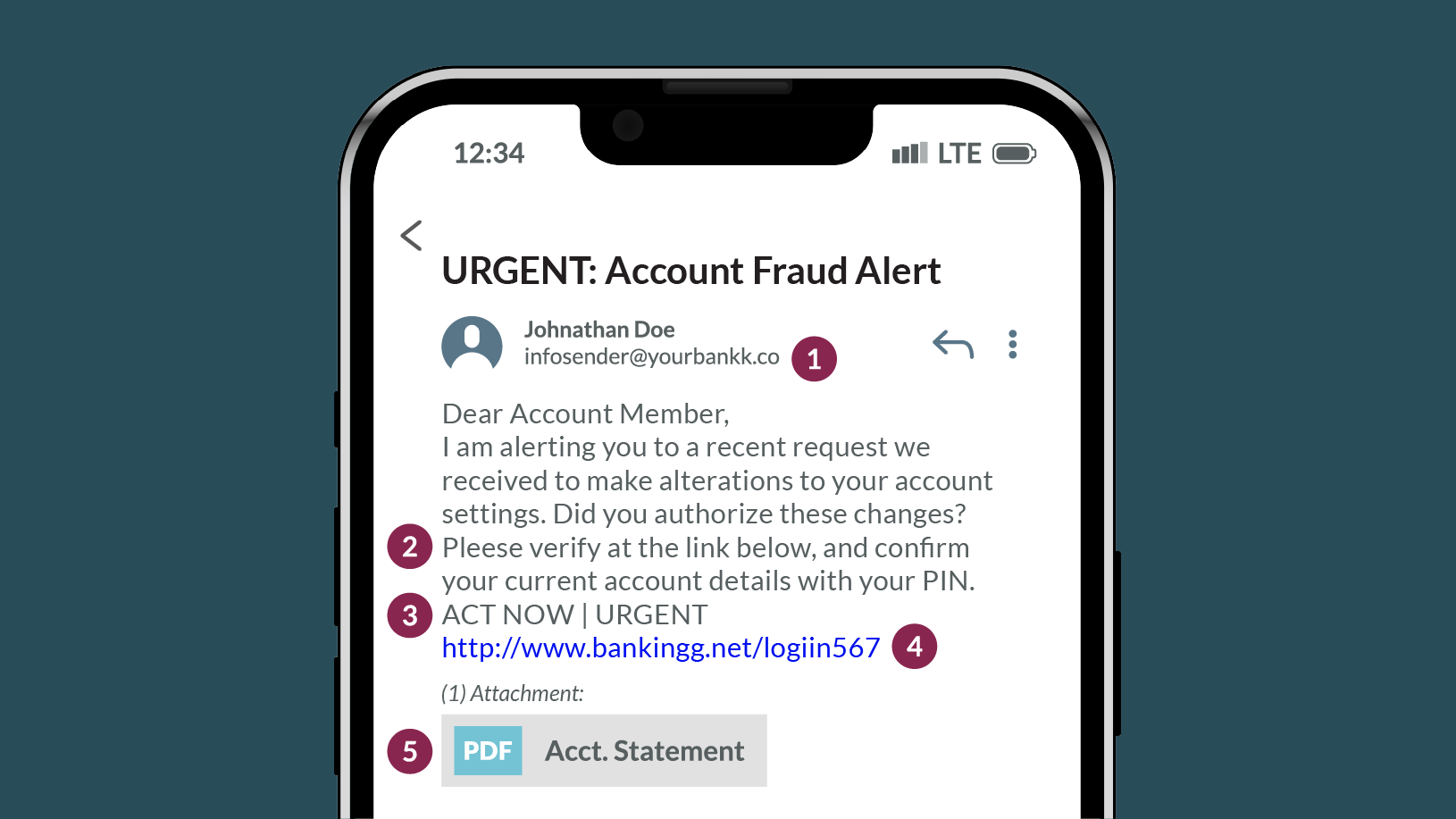
Does that look like an email address your bank would use? Be wary of unexpected emails from addresses that aren’t like the ones your bank typically employs.
If you see misspelled words or odd grammar, they are all clear signs of an impersonator.
If an email uses scare tactics, such as urgent warnings of account closure or security breaches, you can safely assume it’s a scam.
Banks will never ask you to log in via email. Phishing emails use deceptive URLs to take you to malicious websites. Never click links that you weren’t expecting.
Real banks will never send an email attachment — especially when you didn’t ask for it. Attachments can contain malware that can compromise your computer or personal information. Never click on attachments from emails supposedly from your bank.

Request a free annual copy of your credit report at annualcreditreport.com.

Look for these signs indicating a fraudulent email:


More information about tax identity theft is available from the Federal Trade Commission or the IRS.
Act quickly - taking action immediately is important to stop any further damage and to begin resolving any potential issues that could result from identity theft.


Equifax | 800.685.1111| equifax.com
Experian | 888.397.3742 | experian.com
TransUnion | 800.680.7289 | transunion.com
Request a free copy of your credit report and review it carefully for fraudulent activity. If fraud occurred, notify the credit bureau and companies where fraud occurred.

Federal Trade Commission | 877.ID.THEFT(877.438.4338) | www.identitytheft.gov
Create an Identity Theft Affidavit and personal recovery plan.

Bring with you:
Ask to have a copy or the number of the report.

Government Agencies, Social Security Administration, IRS, Postal Service and other companies | www.identitytheft.gov/Top-Company-Contacts

Keep track of your fraud resolution activities.
DOWNLOAD the fraud repair kit - resolution log.Use the Federal Trade Commission's booklet to guide you through the recovery process.
DOWNLOAD the Identity Theft Recovery Plan.We will investigate your claim regardless of documentation presented. However, providing the following information can help us reach a resolution for your dispute more effectively.
Phishing is a type of online scam where criminals make fraudulent emails, phone calls and texts that appear to come from a legitimate financial institution. Every year, people lose hundreds, even thousands, of dollars to these scams. The communication is designed to trick you into entering confidential information (like account numbers, passwords, PINs or birthdays) into a fake website by clicking on a link, or to tell it to someone imitating your financial institution on the phone.
Be aware of these common scam attempts and what they entail:
Emails (Phishing): Scammers send emails that appear to be from legitimate sources, such as banks, social media platforms or well-known companies. These emails often contain links or attachments that, when clicked, can install malware on your device or lead you to fake websites designed to steal your personal information.
Phone Calls (Vishing): Scammers make phone calls pretending to be from trusted organizations, such as government agencies, banks or tech support services. They may try to trick you into providing sensitive information, such as Social Security numbers, bank account details or passwords.
Texts (Smishing): Similar to phishing, smishing involves receiving text messages that appear to be from legitimate sources. These messages often contain links that, when clicked, can lead to phishing sites or download malware onto your device.
QR Codes (Quishing): Scammers use QR codes to direct you to malicious websites or download harmful apps. These QR codes can be found in emails, text messages, or even posted in public places. Always be cautious when scanning QR codes and verify the source before proceeding.
If you suspect that an email or text you receive is a phishing attempt:
If you receive a phone call that seems to be a phishing attempt:
1. Contact your bank, financial institutions and creditors
2. Secure your email and other communication accounts
3. Check your credit reports and place a fraud alert on them
– Experian: 888.397.3742 or experian.com
– TransUnion: 800.680.7289 or transunion.com
– Equifax: 800.685.1111 or equifax.com
4. Contact the Federal Trade Commission to report an ID theft incident: visit identitytheft.gov or call 877.438.4338.
5. File a report with your local law enforcement.

FRAUD PREVENTION

FRAUD PREVENTION

FRAUD PREVENTION

FRAUD PREVENTION